การเพิ่มความปลอดภัยให้ฐานข้อมูล: วิธีการของ One Time Pad
Main Article Content
บทคัดย่อ
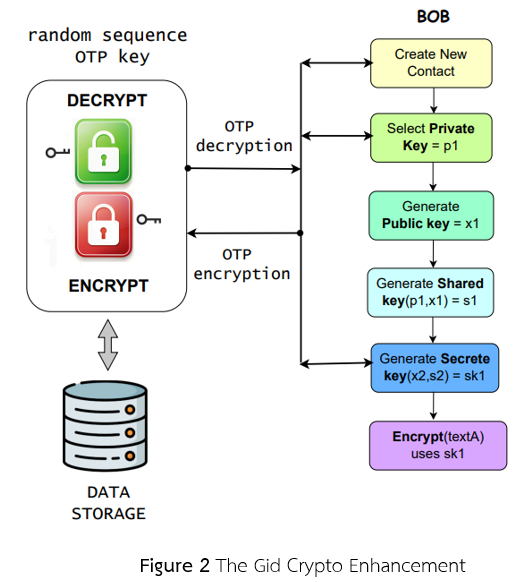
การรักษาความปลอดภัยของข้อมูลที่มีความละเอียดอ่อนซึ่งถูกเก็บไว้ในฐานข้อมูลถือเป็นความท้าทายที่สำคัญที่องค์กรในหลากหลายอุตสาหกรรมต้องเผชิญ ถ้าฐานข้อมูลมีการรักษาความปลอดภัยที่ไม่เพียงพอ จะนำไปสู่การละเมิดข้อมูลหรือการรั่วไหลของข้อมูลที่รุนแรง ซึ่งส่งผลกระทบต่อความเป็นส่วนตัวโดยเฉพาะข้อมูลสำคัญที่เป็นความลับ งานวิจัยนี้มุ่งเน้นไปที่ความสำคัญของมาตราการรักษาความปลอดภัยบนฐานข้อมูล และบทบาทของการใช้เครื่องมือกิดคริปโทในการรักษาข้อมูลให้เป็นความลับ กิดคริปโทเป็นแอปพลิเคชันแบบสแตนอโลนที่สามารถทำการเข้ารหัสและถอดรหัสข้อมูลได้อย่างมีประสิทธิภาพโดยใช้กุญแจส่วนตัว กุญแจสาธารณะ และกุญแจร่วม ก่อนหน้านี้กิดคริปโทจะทำการเก็บกุญแจที่ใช้ในการเข้ารหัสและรายชื่อผู้ติดต่อกันลงในฐานข้อมูลมองโกลดีบีโดยตรง ซึ่งอาจก่อให้เกิดความเสี่ยงด้านความปลอดภัยหากผู้โจมตีระบบสามารถเข้าถึงรหัสผ่านได้ งานวิจัยนี้ได้นำเสนอวิธีการใหม่ที่ใช้ประโยชน์จากการนำวิธีการเข้ารหัสแบบวันไทม์แพด (โอทีพี) เข้ามาร่วม เพื่อยกระดับความปลอดภัยให้กับการใช้งานกิดคริปโท การใช้โอทีพีทำให้ข้อมูลรายชื่อผู้ติดต่อ กุญแจส่วนตัว และกุญแจลับ มีการเข้ารหัสก่อนนำไปจัดเก็บลงฐานข้อมูล ทำให้ข้อมูลไม่สามารถเข้าใจได้หากไม่มีกุญแจที่ใช้ในการถอดรหัสที่ถูกต้อง แม้ว่าจะมีการเข้าถึงข้อมูลเหล่านั้นโดยผู้ที่ไม่ได้รับอนุญาตก็ตาม แอปพลิเคชันกิดคริปโทที่ได้รับการปรับปรุงนี้สามารถรักษาความสมบูรณ์ของข้อมูล เก็บข้อมูลไว้เป็นความลับและรักษาความถูกต้องของข้อมูลเอาไว้ โดยสามารถปกป้องข้อมูลที่มีความละเอียดอ่อนในฐานข้อมูลได้อย่างมีประสิทธิภาพ จากการทดสอบการทำงานของกิดคริปโท ผลการทดสอบยืนยันถึงความทนทานต่อการพยายามโจมตี สามารถทำงานได้อย่างถูกต้องและมีประสิทธิภาพ ทำให้เป็นตัวเลือกในการนำไปใช้งานได้จริงและมีความคุ้มค่าในการนำไปรักษาความปลอดภัยให้กับฐานข้อมูล
Article Details

อนุญาตภายใต้เงื่อนไข Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
วารสารวิทยาศาสตร์และวิทยาศาสตร์ศึกษา (JSSE) เป็นผู้ถือลิสิทธิ์บทความทุกบทความที่เผยแพร่ใน JSSE นี้ ทั้งนี้ ผู้เขียนจะต้องส่งแบบโอนลิขสิทธิ์บทความฉบับที่มีรายมือชื่อของผู้เขียนหลักหรือผู้ที่ได้รับมอบอำนาจแทนผู้เขียนทุกนให้กับ JSSE ก่อนที่บทความจะมีการเผยแพร่ผ่านเว็บไซต์ของวารสาร
แบบโอนลิขสิทธิ์บทความ (Copyright Transfer Form)
ทางวารสาร JSSE ได้กำหนดให้มีการกรอกแบบโอนลิขสิทธิ์บทความให้ครบถ้วนและส่งมายังกองบรรณาธิการในข้อมูลเสริม (supplementary data) พร้อมกับนิพนธ์ต้นฉบับ (manuscript) ที่ส่งมาขอรับการตีพิมพ์ ทั้งนี้ ผู้เขียนหลัก (corresponding authors) หรือผู้รับมอบอำนาจ (ในฐานะตัวแทนของผู้เขียนทุกคน) สามารถดำเนินการโอนลิขสิทธิ์บทความแทนผู้เขียนทั้งหมดได้ ซึ่งสามารถอัพโหลดไฟล์บทความต้นฉบับ (Manuscript) และไฟล์แบบโอนลิขสิทธิ์บทความ (Copyright Transfer Form) ในเมนู “Upload Submission” ดังนี้
1. อัพโหลดไฟล์บทความต้นฉบับ (Manuscript) ในเมนูย่อย Article Component > Article Text
2. อัพโหลดไฟล์แบบโอนลิขสิทธิ์บทความ (Copyright Transfer Form) ในเมนูย่อย Article Component > Other
ดาวน์โหลด ไฟล์แบบโอนลิขสิทธิ์บทความ (Copyright Transfer Form)
เอกสารอ้างอิง
Budiman, M. A., Zarlis, M. and Hafirzah (2021). Implement hybrid cryptosystem using Rabin-p algorithm and One Time Pad to secure images. Journal of Physics: Conference Series, 1898(1), 012037.
Evkan, H., Lahr, N., Niederhagen, R., Petri, R., Poller, A., Roskosch, P. and Troger, M. (2020). Security Evaluation of VeraCrypt. Bonn: Fraunhofer Institute for Secure Information Technology.
Fatima, S., Rehman, T., Fatima, M. Khan S. and Ali, M. A. (2022). Comparative analysis of Aes and Rsa Algorithms for Data Security in Cloud Computing. Journal of Engineering Proceedings, 20(1), 14.
Hammami, H., Obaidat, M. S. and Yahia, S. B. (2020). An Enhanced Lightweight Authentication Scheme for Secure Access to Cloud Data. In Proceedings of the 17th International Conference on Security and Cryptography (SECRYPT 2020) (pp. 102-109).
Ibrahim, S., Zengin, A., Hizal, S., Akhter, A. F. M. S. and Altunkaya, C. (2023). A novel data encryption algorithm to ensure database security. Acta Infologica, 7(1), 1-16.
Indra, Z. and Nabila, R. C. (2023). Implementing the RSA Algorithm and the One Time Pad Algorithm for Text Message Security. Formosa Journal of Science and Technology, 2(1), 379-388.
James, T. (2024). Proton Mail Review 2024 – How is it in Reality?. Retrieved 5 May 2024, from Travelsecurely https://travelsecurely.com/protonmail-review/
Jean, A. and Alherbe, T. (2024). Gid Crypto: Application for End-to-End Encrypt and Decrypt E-mail and Data. Journal of Scientific and Technological Reports, 27(2), 90-102.
KakaSoft (2021). VeraCrypt Review 2021: Price, Feature and Alternatives. Retrieved 12 March 2024, from Kakasoft https://www.kakasoft.com/review/veracrypt-review/
Kumari, A. B., Balaji, H., and Lyengar, N. Ch. S. N. (2023). One Time Pad Encryption Technique in Cryptography. International Journal of Computational Learning & Intelligence, 2(1), 1-7.
Miguel, P. G. (2024). 18 Best Encryption Software. Reviewed For 2024. Retrieved 28 May 2024, from Thectoblub https://thectoclub.com/tools/best-encryption-software/
Ngaogate, W., Jean, A., Wattanataweekul, R., Janngam, K. and Alherbe, T. (2024). Hybrid Machine Learning Algorithm with Fixed Point Technique for Medical Data Classification Problems Incorporating Data Cryptography. Thai Journal of Mathematics, 22(2), 295-310.
Preveil (2024). Simple, Encrypted Email and File Collaboration. Retrieved 10 June 2024, from Preveil https://www.preveil.com/
Rubenking, N. J. (2024). The Best Email Encryption Services for 2024. Retrieved 3 June 2024, from Pcmag https://www.pcmag.com/picks/the-best-email-encryption-services
Shingari, N. and Mago, B. (2024). The Importance of Data Encryption in Ensuring the Confidentiality and Security of Financial Records of Medical Health. In 2024 IEEE International Conference on Interdisciplinary Approaches in Technology and Management for Social Innovation (IATMSI) (pp. 1-6). Gwalior: IEEE.
TrustRadius (2024). Make confident technology decision. Retrieved 7 March 2024, from TrustRadius https://www.trustradius.com/